Introduction
Summary
How was it done ?
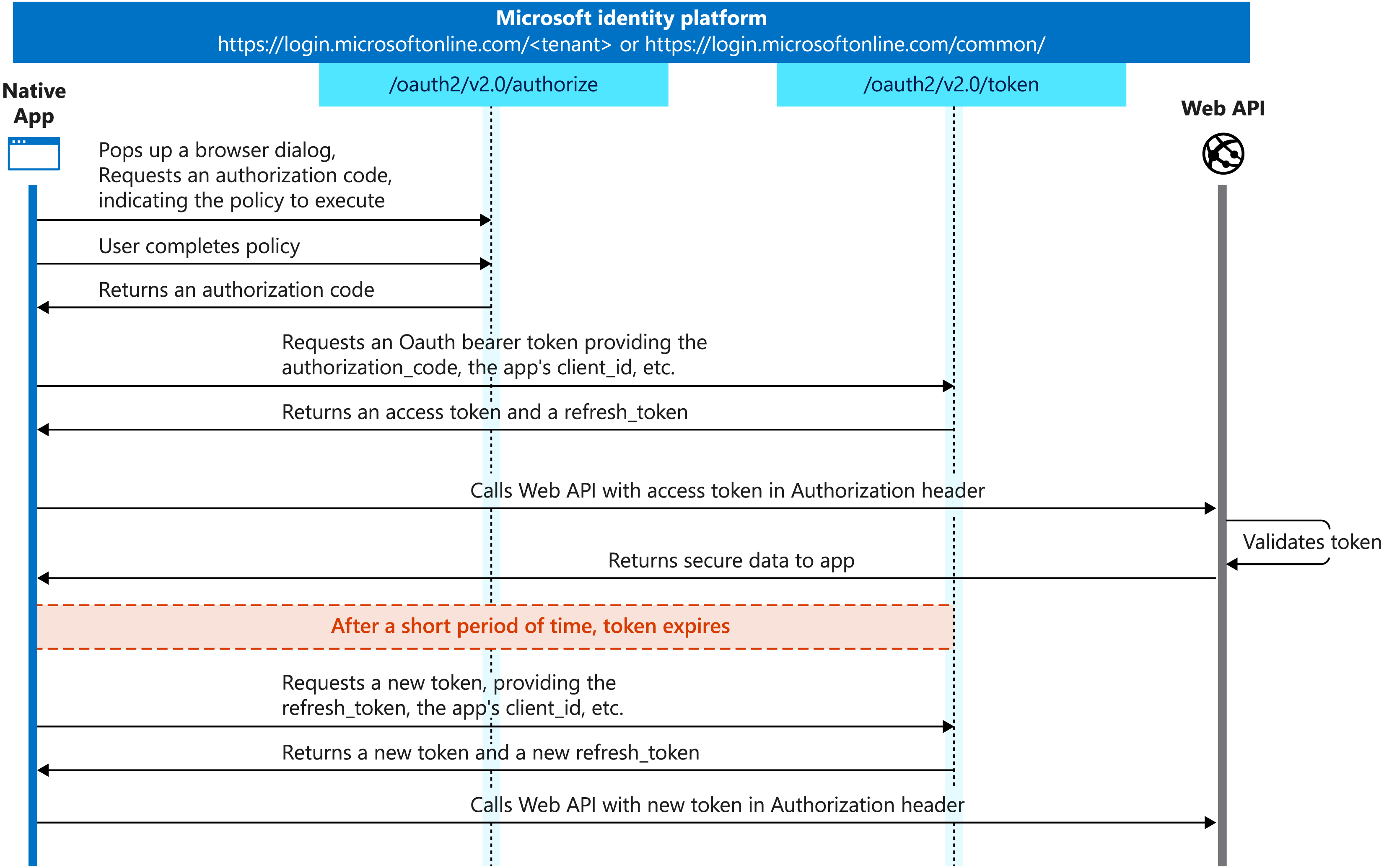
Is it the end ?
2.- No automatic scope validation in the libraries used for token validation, which made enterprise email APIs accepting a consumer key.
Both of these items got corrected, but do we know if only email accounts were impacted ?
Key Take Away
- Check if your organization is compromised, even though Microsoft should have contacted it.
- Now use the Microsoft Purview Audit Premium.
- Ensure that the latest SDK versions are used in the applications.
- Do not locally cache the keys.
- Think about the criticality of the cloud identity providers.
References
(1) https://msrc.microsoft.com/blog/2023/07/microsoft-mitigates-china-based-threat-actor-storm-0558-targeting-of-customer-email/
(2) https://www.cisa.gov/resources-tools/services/secure-cloud-business-applications-scuba-project
(3) https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-193a
(4) https://www.cisa.gov/news-events/news/cisa-and-microsoft-partnership-expands-access-logging-capabilities-broadly
(5) https://www.microsoft.com/en-us/security/blog/2023/07/14/analysis-of-storm-0558-techniques-for-unauthorized-email-access/
(6) https://www.zdnet.com/article/all-eyes-on-microsofts-azure-cloud-numbers-in-q1-fy23/
(7) https://www.zdnet.com/article/microsoft-serves-up-lots-of-teams-numbers-to-demonstrate-growth-except-the-latest-number-of-users/
(8) https://learn.microsoft.com/en-us/purview/audit-premium#audit-premium-events
(9) https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr
(10) https://learn.microsoft.com/en-us/security/operations/token-theft-playbook
(11) https://msrc.microsoft.com/blog/2023/09/results-of-major-technical-investigations-for-storm-0558-key-acquisition/
(12) https://github.com/AzureAD/azure-activedirectory-identitymodel-extensions-for-dotnet
(13) https://github.com/AzureAD/microsoft-identity-web
(14) https://www.microsoft.com/en-us/security/blog/2023/07/19/expanding-cloud-logging-to-give-customers-deeper-security-visibility/

0 Comments